Personal Data ProtectionPersonal Data Protection
Internal management mechanism for personal data protectionInternal management mechanism for personal data protection
We have dedicated personnel in each department to regulate and manage customers’ personal data and hold a review meeting every year to review the relevant management regulations and items managed in a timely manner, to see if there are any measures to be adjusted. HFC has formulated relevant management measures to prevent all security breaches. Employees’ access permissions to or right to retrieve personal information are also restricted.We have dedicated personnel in each department to regulate and manage customers’ personal data and hold a review meeting every year to review the relevant management regulations and items managed in a timely manner, to see if there are any measures to be adjusted. HFC has formulated relevant management measures to prevent all security breaches. Employees’ access permissions to or right to retrieve personal information are also restricted.
Outsourced vendor managementOutsourced vendor management
All outsourced information vendors should obtain ISO 27001 information security certification and need to understand HFC’s high security standards for personal data protection before collaboration. We also carefully evaluate the vendors’ past collaboration records, enterprises served, and capability requirements before collaboration to ensure that both parties have a consensus on customer data security protection before collaborating. In addition, before the outsourced service is suspended or ends, the outsourced vendor should return all relevant personal data and intellectual property used or kept during the service period in accordance with the content of the agreement, then our contact point is responsible for deleting the use, access, and other permissions for such data, to ensure that there are no information security breaches.All outsourced information vendors should obtain ISO 27001 information security certification and need to understand HFC’s high security standards for personal data protection before collaboration. We also carefully evaluate the vendors’ past collaboration records, enterprises served, and capability requirements before collaboration to ensure that both parties have a consensus on customer data security protection before collaborating. In addition, before the outsourced service is suspended or ends, the outsourced vendor should return all relevant personal data and intellectual property used or kept during the service period in accordance with the content of the agreement, then our contact point is responsible for deleting the use, access, and other permissions for such data, to ensure that there are no information security breaches.
Information security managementInformation security management
In response to information security, the Information Department is the main unit responsible for planning and developing the information security of HFC. We have established information security management measures and policies and computerized information system control operations to ensure the confidentiality, integrity and availability of information, protect the Company's information assets from improper use and disclosure, and ensure the security of information collection, processing, transmission, storage and circulation.In response to information security, the Information Department is the main unit responsible for planning and developing the information security of HFC. We have established information security management measures and policies and computerized information system control operations to ensure the confidentiality, integrity and availability of information, protect the Company's information assets from improper use and disclosure, and ensure the security of information collection, processing, transmission, storage and circulation.
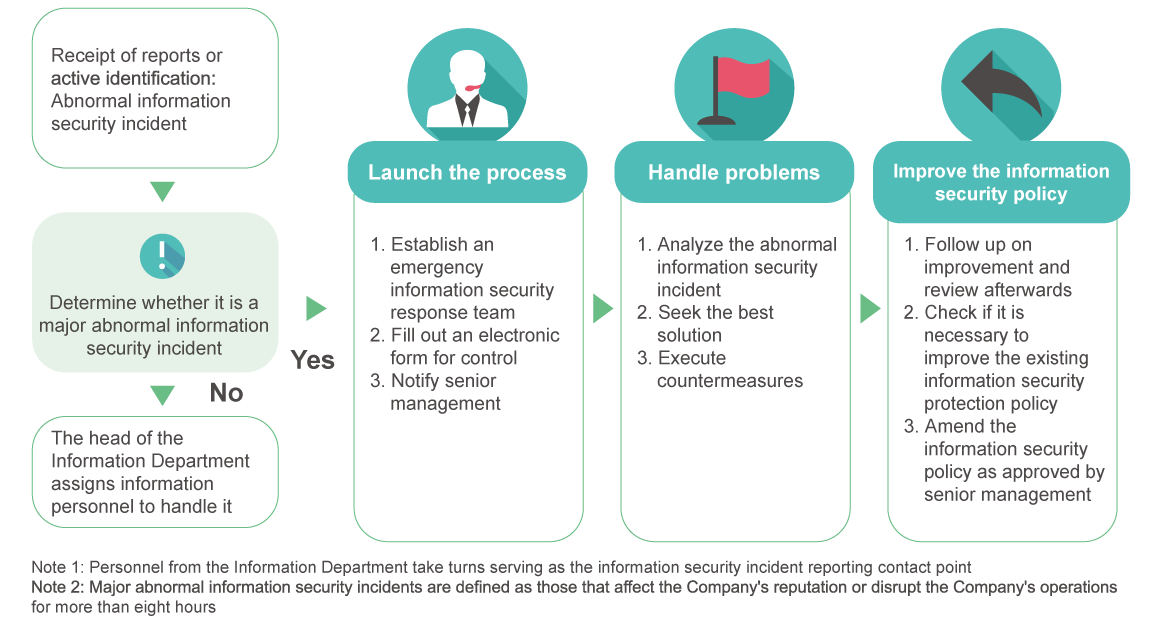
Information security incident reporting processInformation security incident reporting process
| Information security violations in the last three years | 2021 | 2022 | 2023 |
| Number of major information security incidents | 0 | 0 | 0 |
| Number of violations of customer privacy | 0 | 0 | 0 |
| Number of customers affected by information leakage | 0 | 0 | 0 |
| Total fines/penalties paid for information security incidents | 0 | 0 | 0 |
Regularly review information security vulnerabilityRegularly review information security vulnerability
To strengthen all our systems and information security and expand the coverage, we commission an impartial and objective third party to conduct a thorough review of our systems. Therefore, HFC commissions an information security consultant to comprehensively scan the information system for vulnerabilities and rate the overall information security risk level.To strengthen all our systems and information security and expand the coverage, we commission an impartial and objective third party to conduct a thorough review of our systems. Therefore, HFC commissions an information security consultant to comprehensively scan the information system for vulnerabilities and rate the overall information security risk level.
Internal Information Security AuditInternal Information Security Audit
The Information Department arranges regular internal audits every month and every year, and all employees in the group must cooperate. The monthly audit schedule is formulated by the Information Department to audit systems or system functions going live for information security risks, to ensure the normal operation and alignment of new systems or functions with needs. For the annual audit, employees conduct self-check through the "Personal Computer Information Security Checklist".The Information Department arranges regular internal audits every month and every year, and all employees in the group must cooperate. The monthly audit schedule is formulated by the Information Department to audit systems or system functions going live for information security risks, to ensure the normal operation and alignment of new systems or functions with needs. For the annual audit, employees conduct self-check through the "Personal Computer Information Security Checklist".
Third-party audit to strengthen information security operationsThird-party audit to strengthen information security operations
HFC obtained the ISO 27001 Information Security Management System (ISMS) certification in 2022 to ensure the ISMS confidentiality, integrity, and availability. We regularly conduct organizational panorama evaluations of information department system development and maintenance and data center management every year to review the annual performance of 14 information security management and control indicators in ISO 27001. In the meanwhile, HFC has passed the ISO 9001 international quality control certification and operates in accordance with the ISO standards every year. In 2021, professional CPAs were appointed to interview the head of the Information Department to understand the organizational structure and clarify the information unit's responsibilities, and to conduct audits of the three systems and processes below: 1. Randomly check the operation process to ensure that data changes or data retrieval are properly approved in accordance with the procedures 2. Audit whether the relevant software and hardware maintenance plans have been carried out 3. Whether the system authorization is appropriateHFC obtained the ISO 27001 Information Security Management System (ISMS) certification in 2022 to ensure the ISMS confidentiality, integrity, and availability. We regularly conduct organizational panorama evaluations of information department system development and maintenance and data center management every year to review the annual performance of 14 information security management and control indicators in ISO 27001. In the meanwhile, HFC has passed the ISO 9001 international quality control certification and operates in accordance with the ISO standards every year. In 2021, professional CPAs were appointed to interview the head of the Information Department to understand the organizational structure and clarify the information unit's responsibilities, and to conduct audits of the three systems and processes below: 1. Randomly check the operation process to ensure that data changes or data retrieval are properly approved in accordance with the procedures 2. Audit whether the relevant software and hardware maintenance plans have been carried out 3. Whether the system authorization is appropriate
No material information security deficiencies affecting financial reporting were identified as a result of external audits in 2023.No material information security deficiencies affecting financial reporting were identified as a result of external audits in 2023.












